It Company Charlotte Things To Know Before You Get This
When speaking with a potential handled IT service carrier or specialist, go past concerns concerning accreditations or staff dimension. You want to employ the organization that understands how to apply modern technology to enhance your business as well as has the knowledge to make it happen.
Make certain that you recognize what you're spending for and that it covers all present and prospective requirements. Preserving consistent results and also distribution is vital. Your possible handled company should be able and eager to share instances of their policies and processes, and also reveal just how they equate to various service atmospheres.
These are typically glorified break-fix contracts without aggressive surveillance and also assistance or service enhancement plans. You will just see them when something is currently wrong and they will not do a lot, if anything, to stop issues or check out the bigger picture. Lots of likewise don't take notice of IT industry trends and also innovations which can limit their clients to hanging back the competition.
It is crucial to find out if your IT provider is vendor-neutral. If they are acquired or partial to using just certain suppliers' items, some offerings might not necessarily be best for your service. A good MSP needs to always concentrate on selecting the innovation that provides the most effective outcomes for you.
5 Simple Techniques For It Company Charlotte

If you respond to "no" to any of the following inquiries, then you are using a break-fix technique to maintain your network, as well as might benefit from a handled service provider without costing you any type of much more: Do you discover out instantly if your data backup falls short to run? Do you know which equipment on your network is aging and also might require replacing in the next 6 months? Do you have one number to call for all your innovation solution needs?
Any of the firms that make the checklist are recognized as reputable, successful, and innovative. If the service provider you're interviewing has made the list, that's a pretty solid sign you can trust them with your IT needs.
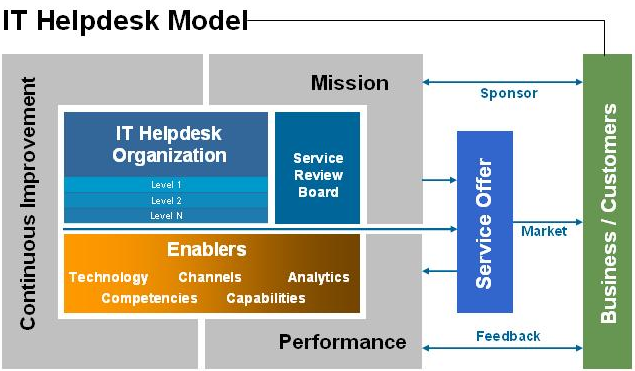
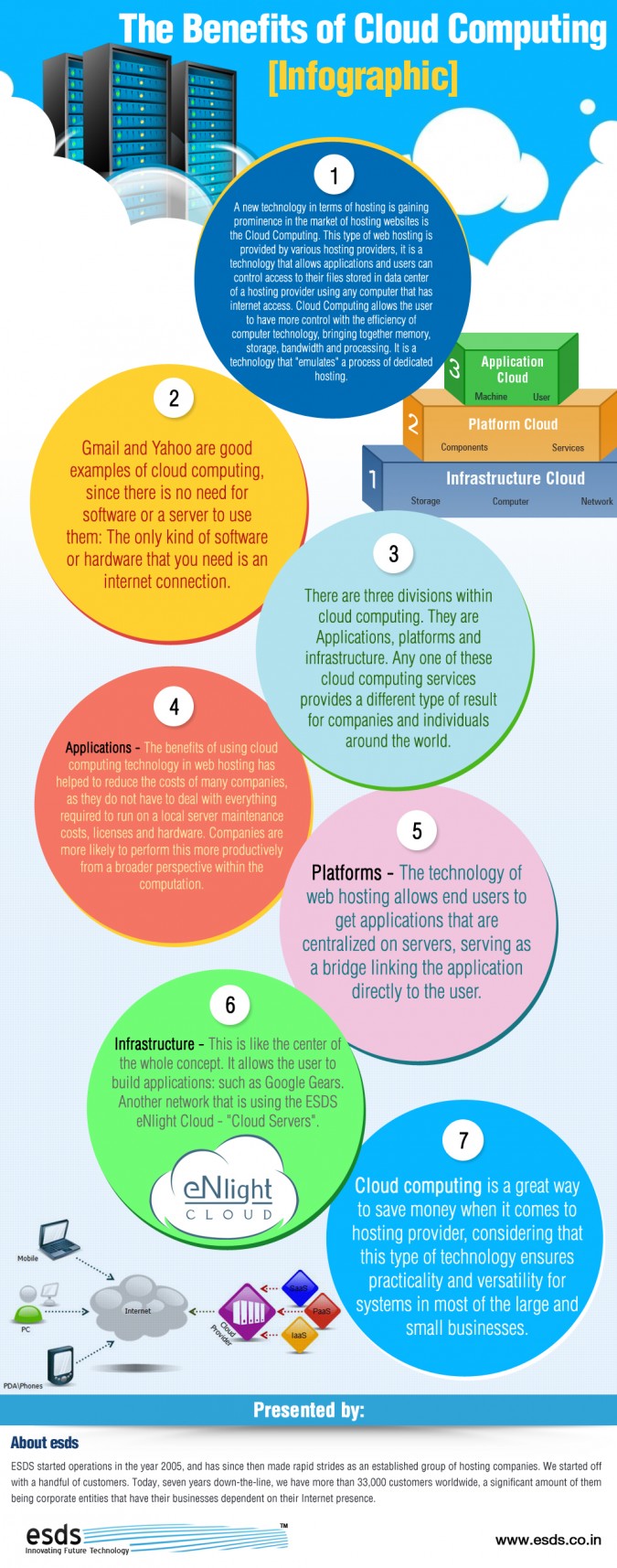
IT Took care of Services is the technique of outsourcing your IT requires to look at more info a Managed Provider (MSP). The MSP delivers innovation and also assistance solutions to organizations at a portion of the price of employing an interior IT team. MSPs can advise, apply, as well as supply on-going management of technology to guarantee IT is straightened with business' tactical objectives.
An internal group will have various inspirations to that of an external/outsourced team. An outsourced provider will certainly more than likely offer a performance-based agreement with crucial metrics that need to be adhered to on a month-to-month basis, whereas an interior resource will certainly be encouraged to prove worth with volume of work.
Cyber Security Charlotte Fundamentals Explained
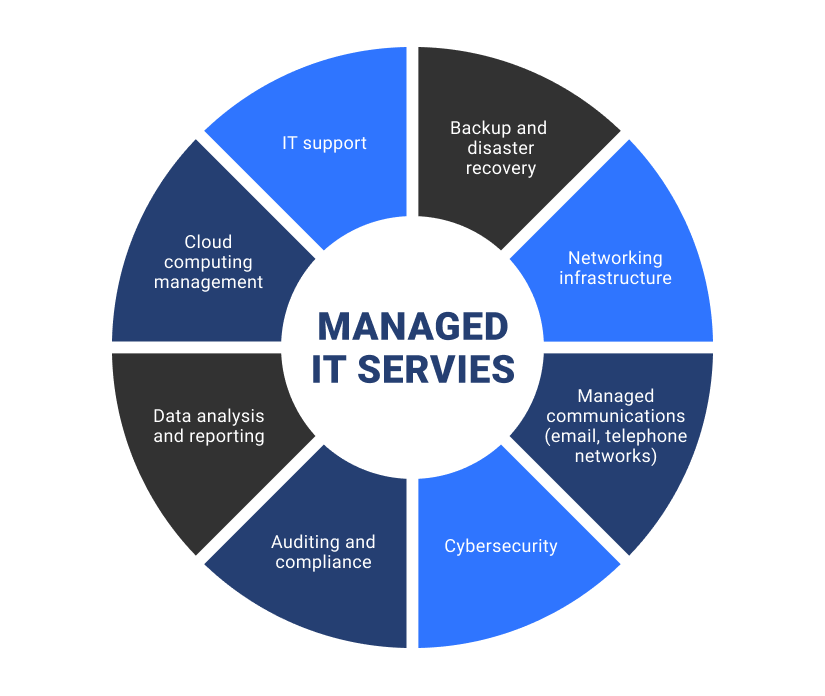
Even fairly simple jobs such as back-up and bring back procedures are easier now to contract out than do inside due to the needs on the helpdesk. MSPs have the range to perform the necessary routine test restore processes needed to make sure that back-ups are really being run and are actually usable. it support charlotte.
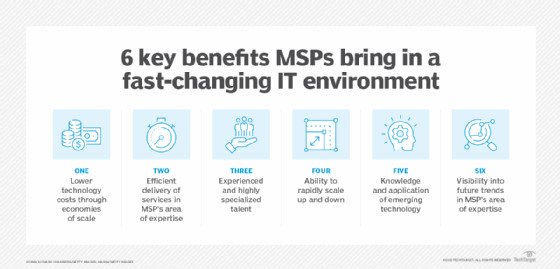
Since the very early 2000s, the landscape has actually grown and adjusted to adjustments in innovation; nevertheless, it continues to be a proactive and also cost-efficient option for little to additional hints mid-size companies. In the 2020s, technology is extra intricate than ever before, with MSPs delivering more customizable remedies to fulfill even more certain requirements.
They can likewise be utilized by bigger companies with full-time technical staff to enhance interior resources with expertise in areas where it's needed but not readily available. Some managed solutions are given by permanent workers image source of a provider (managed it services charlotte). Others involve agreements with third-party firms that designate workers when required for fixings or various other job.
10 Easy Facts About It Company Charlotte Described
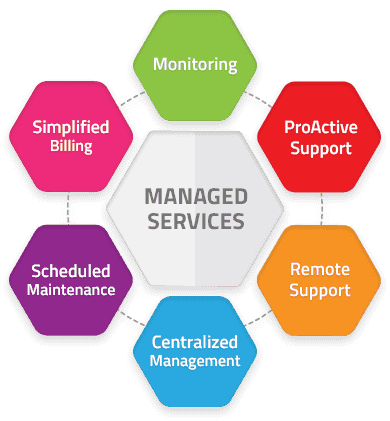
Learn just how much responsibility they'll assume in situation of issues as well as what assistance they'll supply in much less immediate circumstances. With handled solutions, your service's software and hardware are monitored by an external IT staff. This includes safety surveillance for infections and also malware as well as software updates to ensure that everything stays updated.
If a problem is extreme sufficient, they can additionally look after all repair services or substitutes without you needing to fret about it. The managed provider can provide continuous support remotely to ensure your company operations are never interrupted by failures. MSPs use a range of prices designs as well as service levels to define exactly what they will provide you, in addition to supplying defined solution level agreements, such as uptime and responsiveness to problems.